CoViD-19 DID MORE THAN MAKE ILL AND HOSPITALISE!
- bondash
- Apr 17, 2025
- 3 min read
In April 2022, Cashapp found itself at the wrong end of a security incident.
A disgruntled, mean, ex-member of staff downloaded data for 8 million users through CashApp Investing, a stock trading feature accessible through CashApp’s service.
Information that was stolen included:
• Customer names
• Brokerage account numbers
• Stock trading portfolios
• Stock trading activity

The data breach was a significant security risk reflecting a failure to implement thorough Access Control Policies, especially for an employee who no longer worked at Cash App. Moreover, the attack persisted for 4 months during which Cash App failed to detect and/or act on the breach.
Cash App underwent multiple class-action lawsuits for failing to implement proper security measures to protect users’ data.
Similarly, from 2023 to 2024, Flutterwave reportedly lost over $37m to multiple security breaches especially via unauthorised access into their systems.

Anywhere you go or look, several other cases of similar security breaches on major organisations and SMEs are there, with incidents increasing by the day. This trend has been on the rise since the advent of Covid-19 and the attendant adoption of remote/hybrid working models.
WHY IS THIS SO?
Prior to CoViD-19, several organisations invested heavily in Network Access Control (NAC) Solutions to enforce authorised access for ONLY on-premise devices/users to network resources. Afterall, we rarely worked remotely at that time.
During and post-CoViD, NAC suddenly became ineffective as it was not designed to handle cloud-hosted applications and the resultant ubiquity of the corporate data. Numerous organisations also quickly realised that VPNs were not sufficient to consistently & securely cater to remote access towards guaranteeing a flawless end-user experience.
Organisations were thus compelled to adopt ZTNA solutions to accommodate the telecommuters (remote workers).
For CIOs, CTOs, IT administrators and Security Risk Managers, this often meant maintaining siloed security solutions as NAC and ZTNA could not intermingle effectively. Imagine maintenance of separate access policies for both and cloud-based workloads. This can be complex indeed, a situation that should never feature in attempts to guarantee optimal security. Complexity and security are immiscible with each other.
Emergent IT Admin fatigue from the complexity can lead to lapses in management and leave the door ajar for e-miscreants.
In addition, many traditional NAC offerings grant broad network access (not application-only access) and have limited capabilities for adjusting access in near real time in response to changing risk profiles of users.
Should we then wonder why there is a surge of security breaches post-CoViD-19 such as those against Cashapp and Flutterwave above?
Organizations need to move toward Zero Trust at all levels but implementation is challenging.
THE SOLUTION
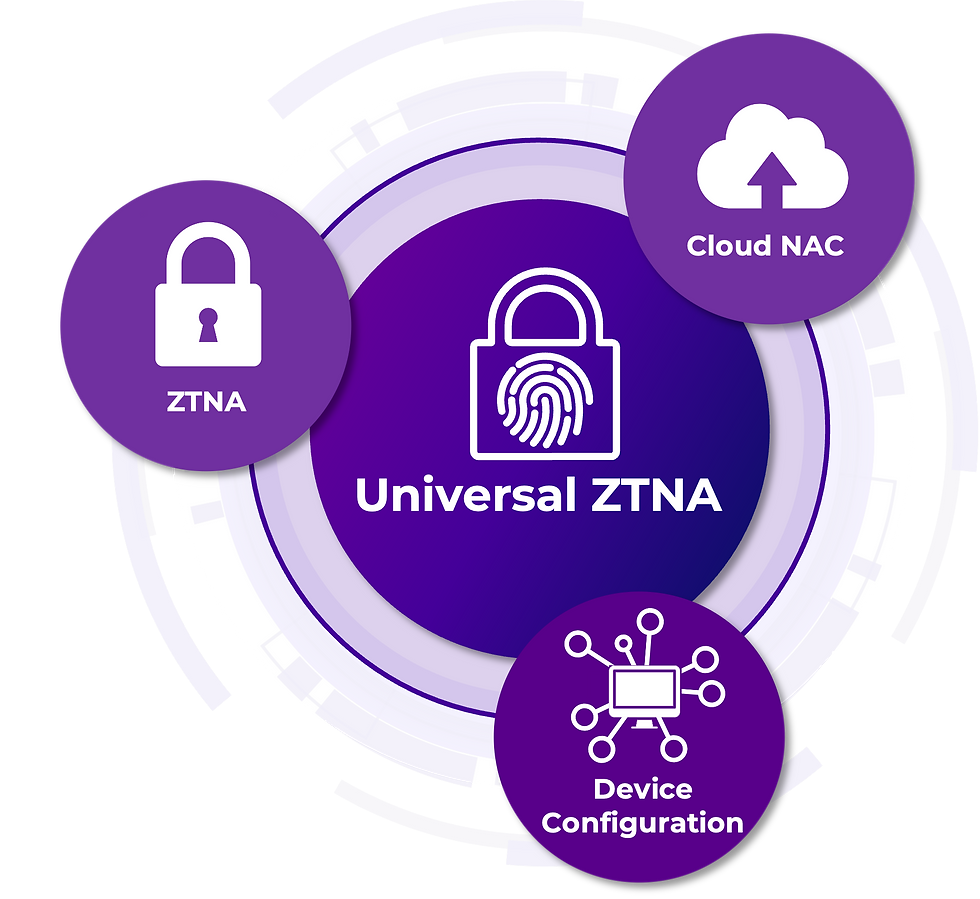
ZTNA is primarily focused on user-based remote access but many vendors such as Extreme Networks now extend that functionality to include branch/campus environments (on-premise) and non-users.
This is known as Universal ZTNA.

These emerging Universal ZTNA (UZTNA) offerings include core NAC functionality, including the ability to authenticate and grant access to devices/users, along with visibility. However, they also provides additional functionality i.e. they enable fine-grained access to only the appropriate resources (i.e., grant access to an application rather than a network).
In addition, leading UZTNA offerings such as from Extreme Networks adjust access dynamically in near real time. Extreme Network’s UZTNA (with NAC as a feature) provides a single management and policy plane to address a hybrid workforce and move toward a Zero-trust Posture.

Extreme Networks boasts of the industry’s most complete UZTNA in a single, easy-to-use SaaS offering, with a single zero trust policy engine which ensures consistency and unified observability. It also extends coverage to IoT devices plus guests’ and contractors’ devices.
Extreme’s Cloud UZTNA is cloud-managed (as name implies), includes automated device configuration, a single reporting interface and single subscription with AI-powered anomaly detection and remediation........
And guess what, when you adopt Extreme's UZTNA, you will not need to replace any existing firewalls!
To learn more about how you can integrate UZTNA into your environment, please contact us via sales@caspian-services.com or 0904-CASPIAN (0904-2277426).
We look forward to having a chat with you!




Comments